Home » Cybersecurity Compliance » CMMC Compliance » CMMC Certification Levels
CMMC Compliance Levels
A Complete Guide for DoD Contractors
- CMMC compliance is mandatory.
- Failure to comply means losing millions in government contracts, while compliance strengthens cybersecurity, protects sensitive data, and builds a competitive edge.
- If your company only handles FCI—unclassified government data not intended for public release—you must meet CMMC Level 1 requirements.
- If your company processes, stores, or transmits Controlled Unclassified Information (CUI), you must achieve CMMC Level 2 certification. This applies to prime contractors and subcontractors working with sensitive DoD projects.
- CMMC Level 3 is required for companies handling critical DoD information, where advanced protection is needed to guard against nation-state cyber threats.
- CMMC isn’t a one-time event—you must recertify and continuously improve security. Companies that fail to maintain cybersecurity standards risk losing DoD contract eligibility.
Get CMMC Ready Today
Why CMMC Matters: Protecting National Security and Your Business
Cyber threats targeting the Defense Industrial Base (DIB) are at an all-time high. Nation-state actors, ransomware groups, and cybercriminals are actively targeting small to mid-sized contractors, knowing they often lack the robust cybersecurity defenses of large primes. The Cybersecurity Maturity Model Certification (CMMC) is the DoD’s solution—ensuring that every contractor handling Federal Contract Information (FCI) or Controlled Unclassified Information (CUI) meets strict security standards before they can bid on or renew contracts.
For defense contractors, CMMC isn’t just a regulatory hurdle—it’s a business necessity. Failure to comply means losing millions in government contracts, while compliance strengthens cybersecurity, protects sensitive data, and builds a competitive edge.
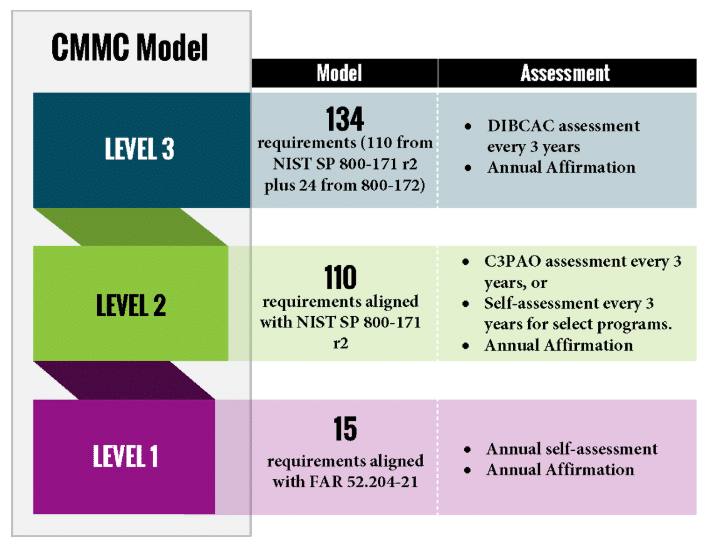
CMMC 2.0 streamlines the framework into three certification levels, each with specific cybersecurity requirements. Understanding these levels and knowing how to prepare for assessment is critical to staying competitive in the defense sector.
CMMC Level 1: Foundational Cybersecurity for Basic Safeguarding
Who Needs Level 1 Certification?
If your company only handles FCI—unclassified government data not intended for public release—you must meet CMMC Level 1 requirements. This applies primarily to small businesses and subcontractors that support DoD contracts but do not handle sensitive CUI. CMMC Level 1 establishes the fundamental cybersecurity practices that all contractors handling Federal Contract Information (FCI) must follow. While this level does not involve the complexity of Controlled Unclassified Information (CUI) protections, it sets the foundation for securing government data and preventing common cyber threats such as phishing attacks, insider threats, and unauthorized access.
Key Requirements of Level 1
- Implements 15 basic security practices derived from FAR 52.204-21.
- Focuses on basic cyber hygiene. While Level 1 does not require advanced cybersecurity measures, the DoD expects contractors to implement basic security best practices, including password security, access controls, and network security.
- Requires an annual self-assessment (no third-party certification required). Unlike CMMC Level 2, which mandates third-party assessments, Level 1 companies can self-assess their compliance. However, this does not mean the process should be taken lightly.
Common Pitfalls of Level 1 Compliance (and How to Avoid Them)
Even though Level 1 focuses on basic cybersecurity, many companies still struggle to meet compliance. Here are some of the most common mistakes contractors make—and how to fix them.
Thinking Small Businesses Are Exempt
Myth: “We’re just a small subcontractor—CMMC doesn’t apply to us.”
Reality: If you handle any FCI, you must comply with Level 1.
Many small businesses assume cybercriminals only target larger companies—but DoD supply chain attacks often start with the weakest link. Hackers exploit small, under-protected subcontractors to gain access to prime contractors and DoD systems.
Solution: Even if your company only supports a prime contractor, implement at least the 15 FAR security controls to avoid compliance violations and contract risks.
Weak Security Documentation
Problem: “We follow cybersecurity best practices—but we don’t have written policies.”
Why This Fails: Assessors require proof that security controls are properly implemented.
Many companies have basic protections in place (like strong passwords and antivirus software) but fail to document their policies. This creates compliance gaps and puts businesses at risk of contract suspension.
Solution: Maintain a formal cybersecurity policy that includes:
- Who has access to FCI and how it’s controlled.
- How security incidents are reported and managed.
- How often security policies are reviewed and updated.
Did You Know? Contractors must retain security records for 3 years in case of a DoD assessment.
Misconfiguring Access Controls
Problem: Employees have unrestricted access to contract-related data.
Risk: A single compromised account could expose all FCI within your organization.
Many businesses fail to properly restrict access to sensitive data. For example, if every employee can access contract files, one phishing attack could expose critical government information.
Solution: Follow the principle of least privilege—granting employees only the access they need to do their jobs.
- Create role-based access levels to ensure only authorized personnel can view FCI.
- Disable inactive accounts immediately when employees leave the company.
- Use multi-factor authentication (MFA) for logging into FCI systems.
Example: If an intern does not need access to DoD contract data, their account should not have permission to view it.
How Alluvionic Helps You Meet Level 1 Standards
- Guided Self-Assessments – We walk you through every step, ensuring nothing is overlooked.
- Policy & Procedure Development – We create clear, concise security policies that meet DoD standards.
- Security Awareness Training – Employees play a critical role in cybersecurity—we ensure they’re trained to prevent breaches.
CMMC Level 2: Advanced Security for Handling CUI
Who Needs Level 2 Certification?
If your company processes, stores, or transmits Controlled Unclassified Information (CUI), you must achieve CMMC Level 2 certification. This applies to prime contractors and subcontractors working with sensitive DoD projects.
Key Requirements of Level 2
- Implements 110 security controls based on NIST SP 800-171 rev2.
- Requires stronger cybersecurity protections, including:
- Multi-factor authentication (MFA) for all privileged accounts.
- End-to-end encryption of CUI.
- Strict access control measures (least privilege).
- Continuous system monitoring and incident response plans.
- Introduces bifurcation, meaning some contractors must undergo third-party certification while others can self-assess.
Who Can Self-Assess for CMMC Level 2?
Under CMMC 2.0, the Department of Defense (DoD) introduced a bifurcated approach for Level 2 compliance, meaning some companies can self-assess, while others must undergo a third-party certification assessment by a Certified Third-Party Assessment Organization (C3PAO).
Self-Assessment Eligibility for Level 2
A company may self-assess for CMMC Level 2 if it:
- Handles CUI that is NOT considered critical to national security (low-priority CUI).
- Is working under contracts that only require a self-assessment (as specified by the DoD).
- Submits its self-assessment results annually to the Supplier Performance Risk System (SPRS).
- Has a senior company official sign off on the self-assessment, affirming compliance.
Who Must Undergo Third-Party Certification?
Companies must obtain a third-party CMMC Level 2 assessment if they:
- Handle high-priority CUI (e.g., information vital to national security).
- Are working on contracts requiring a formal C3PAO certification (per the contract terms).
- Are in the supply chain of a prime contractor that requires external validation of security controls.
How Do You Know if You Can Self-Assess?
The DoD will specify in each contract whether self-assessment is sufficient or if a third-party assessment is required. If your contract explicitly states a C3PAO certification is necessary, you cannot self-assess.
Challenges Companies Face in Achieving Level 2 Compliance
Underestimating the Scope of CUI
Many contractors believe only specific systems handling CUI are in scope. However, laptops, cloud environments, and mobile devices used in contract work may need to meet CMMC requirements.
Tip: Define your CUI boundaries early. Segmenting your network can reduce compliance scope—and costs.
Poor Documentation & Policy Gaps
Even if cybersecurity measures are in place, poor documentation can cause an assessment failure. The DoD expects detailed security policies, plans, and proof of implementation.
Tip: Ensure your System Security Plan (SSP), Incident Response Plan, and Plan of Action & Milestones (POA&M) are up to date and assessment-ready.
Inadequate Incident Response Planning
A cyber breach doesn’t mean automatic failure, but failing to document and test incident response plans does.
Tip: Conduct tabletop exercises and train employees on incident response procedures.
CMMC Level 3: Expert-Level Security for High-Sensitivity Contracts
Who Needs Level 3 Certification?
CMMC Level 3 is required for companies handling critical DoD information, where advanced protection is needed to guard against nation-state
cyber threats.
Key Requirements of Level 3
- Implements additional controls from NIST SP 800-172.
- Requires enhanced security measures, such as:
- Zero-trust architecture.
- Real-time threat detection.
- Advanced penetration testing.
- Third-party assessments conducted by the DoD’s Defense Industrial Base Cybersecurity Assessment Center (DIBCAC).
Important Note: The DoD is still refining Level 3 requirements, but companies should focus on achieving full Level 2 compliance first.

Maintaining Compliance: CMMC Is a Long-Term Commitment
CMMC isn’t a one-time event—you must recertify and continuously improve security. Companies that fail to maintain cybersecurity standards risk losing DoD contract eligibility.
How to Stay Compliant Year After Year
- Perform Annual Self-Assessments – Identify new risks before they become a problem.
- Keep Security Policies Up to Date – Cyber threats evolve—your defenses should too.
- Train Employees Regularly – A single human error can lead to a compliance failure.
How Alluvionic Helps You Maintain Certification
- Continuous Monitoring & Compliance Support – Ongoing assessments, threat detection, and risk assessments.
- Annual Security Training & Policy Updates – Keeping your team ready for evolving cyber threats.
- Proactive Recertification Planning – Stay ahead of the three-year renewal cycle.
Final Takeaway: Don’t Let Compliance Challenges Cost You DoD Contracts
CMMC certification is mandatory for DoD contractors. Whether you need Level 1 self-assessment support or full-service Level 2 certification prep, Alluvionic is your trusted partner for CMMC success.
Set Your Business Up For Success
The race to compliance has already begun—don’t fall behind. Alluvionic’s experts provide cybersecurity support and focused change management. We minimize disruptions, ensure smooth adoption, and set your business up for success.
Read From Our Blog

CMMC DFARS Rule Now in Effect: Do You Need to Certify?
What to Know About the November 10 Rule You may have heard that November 10, 2025 was a big day for cybersecurity compliance in the

The 6 Biggest CMMC Questions Everyone’s Asking in 2025 – Insights from Our CMMC Webinar
ICYMI: Insights from Our Webinar — CMMC Contract Clause DFARS 252.204-7021 Explained The CMMC landscape shifted in a major way with the release of DFARS

Alluvionic Named PreVeil CMMC Proven Partner, One of Five Recognized to Date
Alluvionic Named PreVeil CMMC Proven Partner Alluvionic has been selected as a PreVeil CMMC Proven Partner, a designation awarded to partners who either received a
Download Our CMMC Readiness Toolkit
Take the guesswork out of compliance. From checklists to assessment guides, our toolkit gives you the practical resources you need to start preparing for certification and secure your defense contracts.

Whether you need project management, process improvement, cybersecurity, product development, training, or government services, Alluvionic has the expertise to provide Peace of Mind and Project Assurance®.

