
Is Your Company Losing Proposal Points Without Knowing It?
How CMMC is Reshaping Proposal Scoring, Teaming, and DoD Access CMMC Level 2 is rapidly changing how defense contractors compete. It is no longer confined
CMMC is here! Register for our free webinar with guests from C3PAOs – Nov 18 @ 1PM EST. Save Your Spot →
Home » Cybersecurity Compliance » CMMC Compliance » What is NIST 800-171?
Are you compliant?
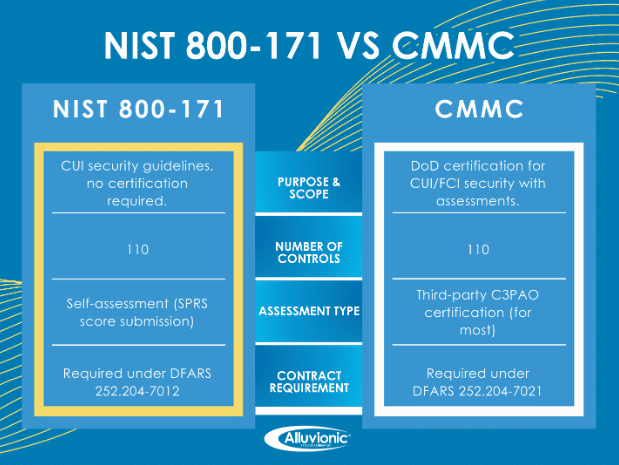
The National Institute of Standards and Technology (NIST) Special Publication (SP) 800-171 rev2 is a set of cybersecurity guidelines that define how Controlled Unclassified Information (CUI) should be protected in non-federal systems. The Department of Defense (DoD), General Services Administration (GSA), and NASA require, or are planning to require, contractors and subcontractors to implement these controls to safeguard sensitive information shared with the federal government.
NIST 800-171 serves as the foundation for the Cybersecurity Maturity Model Certification (CMMC), which builds upon its requirements to ensure compliance within the Defense Industrial Base (DIB). If you’re a government contractor handling CUI, you must meet these standards to win and maintain DoD contracts.
Since DFARS 252.204-7012 mandates compliance with NIST 800-171, contractors must implement these requirements to be eligible for Department of Defense contracts.
CMMC Level 2 is directly based on NIST 800-171, meaning that full compliance is necessary for companies seeking CMMC Level 2 certification.
NIST 800-171 establishes strong cybersecurity best practices to protect sensitive CUI from cyber threats and adversaries.
DFARS are a set of regulations designed to ensure defense contractors maintain adequate cybersecurity measures. We cover the ins and outs of DFARS requirements here.

What About NIST 800-171 Rev 3?
Getting Started with NIST 800-171 Compliance
First, check out our article, “What is SPRS” for a quick guide on SPRS, how to create an account, and how to submit your data. SPRS is a risk management tool that helps organizations meet Defense Federal Acquisition Regulation Supplement (DFARS) 252.204-7019 and 252.204-7012 compliance. Once you have established the appropriate account access in the SPRS, it’s time to take the assessment. Often – when a company commences completion of the self-assessment, they aren’t sure what to do and may not understand what is being asked with the controls.
The simple answer is – a company should determine if each control is implemented, partially implemented, or not implemented. The assessment score starts at a perfect 110, and points are deducted for each area of deficiency for a possible score of negative 203. The controls are weighted at 1 point, 3 points, or 5 points, depending on their criticality.
To complete the assessment, it is imperative that your organization understands what the controls mean in order to determine if they are implemented in your environment. This can be tricky if you aren’t a cyber pro. The Defense Industrial Base Cybersecurity Assessment Center (DIBCAC) curated a list of the top NIST 800-171 requirements that have been determined as other than satisfied (OTS) during DIBCAC assessments.

Below, find a deep dive into four of those most commonly non-compliant controls to help you get on track; Multi-factor authentication, Risk Assessment, Incident Response, and FIPS Validated Encryption.
1. Identification and Authentication (IA) 3.5.3 – Multi-Factor Authentication
To protect CUI, it’s important to limit access to authorized users, to do this effectively you need to verify the identity of those users. That is where multi-factor authentication comes into play. Multi-factor Authentication is the means used to confirm the identity of a user, process, or device, a system which requires more than one distinct authentication factor for successful authentication. Multi-factor authentication includes three factors; something you know, such as passwords and personal identification numbers; something you have, such as a cryptographic identification device token; or something you are, such as biometrics. Authentication uses two or more different factors to achieve authentication.
2. Risk Assessment (RA) 3.11.1 – Periodically Assess Risk
The DoD expects organizations handling CUI to annually assess organizational risk as a means of keeping information safe. So, what are the best practices your organization should consider implementing to comply with this control? First, the control references “periodic” assessments. These should be conducted at a minimum of an annual basis to support the development of a risk management plan. Consider the following as part of your risk assessment process:
3. Incident Response (IR) 3.6.3 – Test Your Incident Response Capabilities
The Incident Response requirements within the NIST 800-171A and Cybersecurity Maturity Model Certification (CMMC) v2.0 framework requires an organization seeking certification to establish and test an operational incident-handling capability for organizational systems that includes preparation, detection, analysis, containment, recovery, and user response activities.
With ever-evolving threats, incident response testing capabilities have become necessary components of information security programs. IR testing can include tabletop exercise, functional exercises, and tests which simulate attacks to examine your incident response procedures:
4. System Communications & Protection (SC) 3.13.11 – FIPS Validated Encryption
This is number one on DIBCAC’s list of most commonly non-compliant controls, and for good reason. A FIPS-validated cryptographic module is one that has been tested and approved by a NIST-approved laboratory per the Federal Information Processing Standard (FIPS) 140-2 U.S. Government standard. The NIST 800-171 control 3.13. 11 requires FIPS-validated cryptography to be used when protecting the Controlled Unclassified Information – whether you are storing it in your system(s) or transmitting it across the internet. Cryptography is the use of mathematical algorithms to ensure secure data communication. Encryption is the process of applying a cryptographic algorithm on data to transform into a new form that only an authorized party is able to understand. It’s like wrapping that sensitive information up in a bubble so that only desired and authorized recipients of the data can access it.
So, how do you comply with this standard? You will need to implement FIPS Validated Encryption in your systems that handle CUI. You will need to document this in policy, process and procedural documents – AND in your System Security Plan. BitLocker is an example of a FIPS-validated system, but it requires a setting before encryption that ensures that the encryption meets the standards set forth by FIPS 140-2.
We’ve helped dozens of companies complete the NIST Basic Assessment. Our experts guide you through each control, assess your score, document compliance, and provide clear next steps.
If you’re looking to learn more, check out our articles on the basics of CMMC or What is SPRS.
Let’s talk about how Alluvionic can support your goals.

How CMMC is Reshaping Proposal Scoring, Teaming, and DoD Access CMMC Level 2 is rapidly changing how defense contractors compete. It is no longer confined

ICYMI: Insights from Our Webinar — CMMC Contract Clause DFARS 252.204-7021 Explained The CMMC landscape shifted in a major way with the release of DFARS

Alluvionic Named PreVeil CMMC Proven Partner Alluvionic has been selected as a PreVeil CMMC Proven Partner, a designation awarded to partners who either received a






It’s simple. A project that gets off on the right foot is likely to take a successful journey. So why do so many projects fail? Use this checklist to assure your project succeeds from the beginning.

Whether you need project management, process improvement, cybersecurity, product development, training, or government services, Alluvionic has the expertise to provide Peace of Mind and Project Assurance®.